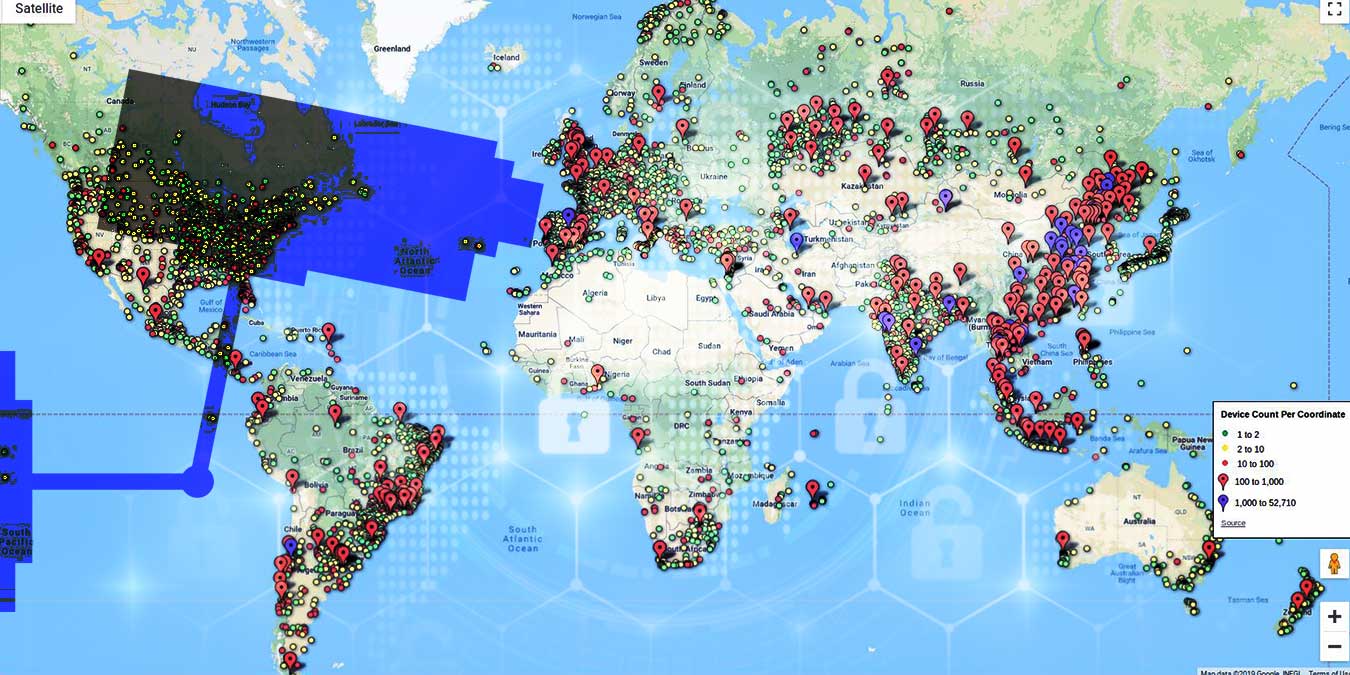
Cameras have been in our phones and computers for quite a while now, but the proliferation of IoT devices is spreading them even further. Home security systems, doorbells, smart TVs, baby monitors, and even pet feeders are streaming live feeds directly to the Internet, and a lot of them have little to no security, making them extremely vulnerable to hijacking and surveillance.
Note that computer webcams aren’t the main focus here. If you want to follow FBI director James Comey and Facebook CEO Mark Zuckerberg’s leads and tape up your device cams, that’s a different issue. Your laptop and phone can still be hacked but should have much better security than your average $20 IP camera.
Hacking risks
There are a few things that a good IP/IoT camera setup should do to remain secure:
- Use strong, unique passwords (not factory defaults)
- Use encryption by default
- Get regular firmware updates
- Run on a separate network
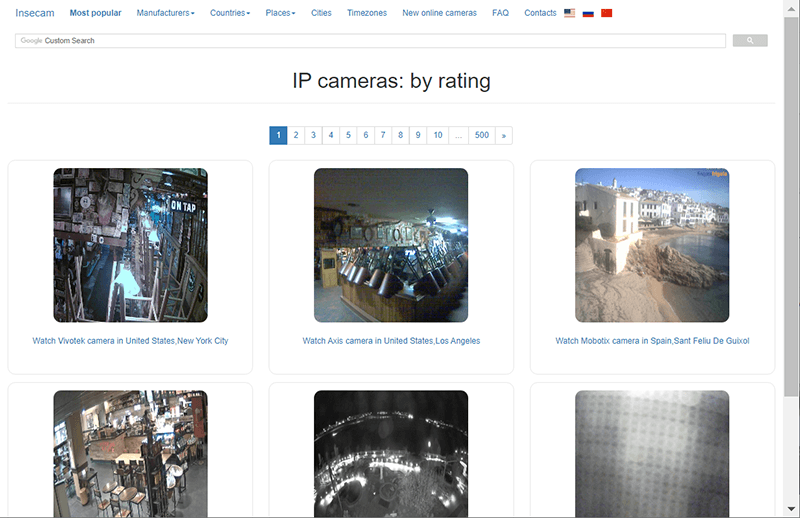
Sites like Insecam or Shodan, however, are tangible proof that a lot of cameras and their users probably aren’t doing those things. A single white-hat hacker found over 15,000 connected cameras with no additional security at all – not even a password.
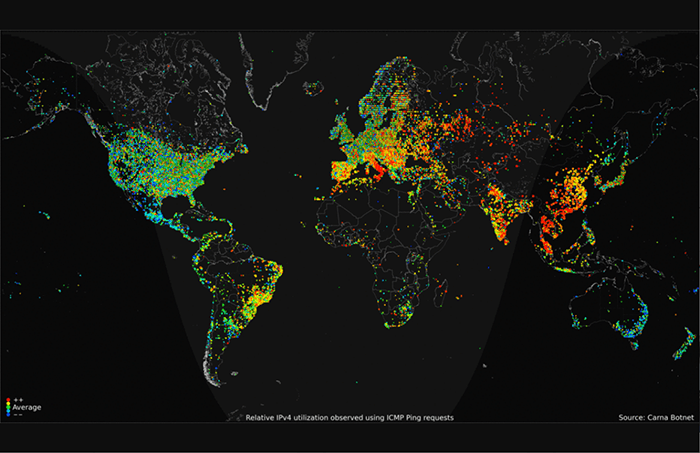
Then there’s the 2016 Mirai Botnet, which had a field day with weakly-secured IoT cameras. These devices are great for botnets, as they have good processing power, weak security, high-bandwidth connections, and low levels of user interaction. Add in an ever-growing list of vulnerabilities like the holes found in Nest Cam and the iLnkP2P protocol (up to 2 million Chinese-made cameras compromised), and you have a perfect storm of hackability.

If cameras are so hackable, then, could someone be watching through them? Basically, yes: if your camera is directly connected to the Internet and protected by weak security, it’s possible that someone could be snooping through it.
But don’t panic! Odds are good that even if your camera is hacked, no one is watching. Most camera feeds are pretty boring, and it’s generally infeasible for human attackers to monitor them waiting for something to happen. AI might eventually change that, but it’s not a concern at the moment.
Bottom line: unless someone is specifically targeting you (which is not impossible), it’s not likely that your IP cameras are streaming live feeds of you to audiences of popcorn-munching cyber-criminals. Unless you happen to catch one pointed at a cash register, computer keyboard (both places you might be able to catch payment info as it’s being entered), or heavily-trafficked/sensitive area, the utility of an individual camera as an entertainment/blackmail device is pretty low.
Having your camera vulnerable still puts your entire network at risk and allows hackers to use its computing power for other things, though, so it’s still an excellent idea to tighten up security.
How to avoid having your camera hacked

- Change the default password! Almost anything is better than the factory default, but it’s always best to go with something strong and unique. Trend Micro estimates that they’ve blocked five million camera hack attempts, 75% of which were brute-force password attacks.
- If the camera has a Web-based interface, see if you can configure it to only allow specific IP or MAC addresses to access it.
- If the settings contain encryption options, enable them. Low-end cameras might not implement them properly, but it’s something.
- If firmware updates are available, download and install them regularly.
- Buy from a reputable manufacturer. If you care about security, unfortunately, you’ll probably have to pay a premium for it.
- Create a separate network (VLAN) on your router for your cameras to use. This won’t necessarily stop them from being hacked, but it’ll help prevent your cameras from exposing the rest of your network.
Big brother might be watching

Encryption? Check! Strong password? Check! Separate network? Check! You’re safe now!
That is, unless your camera happens to be constantly sending video to a large company that has trouble keeping its fingers off your data. If you have the Amazon Ring doorbell, for example, Amazon’s terms of service give it the right to store and use any video the device captures without your permission.
They’ve already used some to help train machine vision algorithms and have featured some in their advertisements. What’s really ruffled people’s feathers, though, is the fact that Amazon has set up a program that gives U.S law enforcement access to a map of Ring cameras and allows them to contact users to ask for access.
So the hackers might not be watching, but there’s a very real possibility that the company that sold you the camera is. Given what we know about the NSA’s past spying programs (like recording Yahoo video chats) and current police interest in surveillance technologies, there’s a good chance that governments are also looking to get in on the action.
Bottom line: Security does not equal privacy
Millions of IoT cameras have been hacked due to weak security and unpatched vulnerabilities, so security on this front clearly isn’t great. If you want to use an IoT device with a camera, though, taking proper security steps will go a long way toward ensuring that nobody can access your feed.
The bigger problem may end up having more to do with the invited guests than the uninvited ones, though. If you don’t want your doorbell reporting back to Amazon (and possibly to local law enforcement), your only option is not to get an Amazon doorbell.
Image credits: Ring video doorbell, NWSC, Hacked Camera, Carna Botnet
Get the best of IoT Tech Trends delivered right to your inbox!









