Shadow IoT is the active use of unauthorized IoT networks, devices or sensors without the IT team knowing it. A good example of this is the days where employees would bring their mobile devices and personal smartphones to the office and use them for work purposes.
There are several threats this brings to a company in terms of security and other aspects as we shall see in this post. Follow along to find out more about the prevalence, risks, and how to mitigate Shadow IoT at your workplace.
Prevalence of Shadow IoT
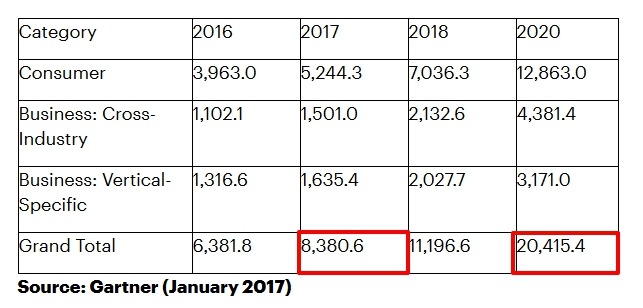
Shadow IoT’s prevalence results from the fact that billions of IoT devices are in use globally. According to Gartner, the number is predicted to rise from 8.4 billion in 2017, to a whopping 20.4 billion IoT devices in 2020 worldwide.
At the workplace, employees connect not only their personal mobile devices to the company network, but are also using smart devices like thumb drives, speakers, and much more.
In fact, a 2018 report by Infloblox reveals that on a typical day, over a thousand Shadow IoT devices connect to networks in a third of companies in the U.S., UK, and Germany. Majority of the devices are digital assistants, fitness trackers, gaming consoles, smart TVs and smart kitchen appliances.

Similarly, office buildings are increasingly being upgraded with IoT devices such as air conditioning and heating IoT sensors controlled by smart thermostats.
Vending machines on business premises are also connected via Wi-Fi to the web, and these increase the prevalence of Shadow IoT when they’re connected to the company network without the IT team knowing or even being aware of it.
The Risks of Shadow IoT
Shadow IoT poses great risks to a company because IT cannot secure or control the devices that aren’t visible on the network. Additionally, these devices are easy targets for online snoopers and hackers, resulting in a surge in IoT attacks.

IoT devices are often set up using default user names or IDs and passwords, lack inherent, enterprise-grade security controls, and tend to be added to a company’s network without informing the IT team.
Further, connected devices are vulnerable to cybercriminals as they’re easily discoverable via search engines like Shodan that provides details of identifiable devices. As such, it’s easier for criminals to identify many devices on company or enterprise networks and target them for vulnerabilities.
One of the popular examples of hacker attacks on Shadow IoT devices is the 2016 Mirai botnet attack that saw home network routers and Protocol (IP) cameras hacked. The aim was to build a massive botnet army, which executed disruptive DDoS attacks that led to no internet access in much of the U.S. East Coast.
Most Shadow IoT devices are therefore not secure because they’re mainly focused on a few tasks and lack security features over and above WPA2 WiFi. Some of these devices don’t even offer a process through which you can report potential vulnerabilities.
Hackers can also exploit unsecured IoT devices for ransomware attacks and data exfiltration. One of the strange types of IoT attacks happened when criminals hacked into a casino’s network by accessing a smart thermometer inside a fish tank in the lobby.
They stole the casino’s high-roller database once they accessed the network, and such are the kinds of IoT-enabled attacks that IT security teams and CSOs worry over.
Shadow IoT introduces new protocols, operating systems, and wireless frequencies such that companies that rely on legacy security technologies can’t see the imminent threats to their businesses.
What to Do About Shadow IoT and Its Risks
In order to mitigate and deal with Shadow IoT and its threat to an organization, below are some measures you can take:

- Educate your team about the threat of Shadow IoT and get buy-in on critical security measures and IoT policies.
- Create policies that enable members of the organization to connect their IoT devices and networks easily to the company’s network with approval and support of the IT team. Don’t outrightly ban IoT devices, but fast-track approvals where feasible and whenever possible to reduce presence of Shadow IoT.
- Have separate networks to support approved Shadow IoT gadgets and ensure your main enterprise networks are protected as much as possible.
- Check connected devices and networks regularly while searching for any unknown devices on all your company’s networks. Proactively looking for Shadow IoT devices is important because most of them don’t live on the company network, but are wireless-enabled. Doing this allows for asset management and visibility of the devices and networks.
Wrap-Up
The growing use of personally owned IoT products at the workplace is making it increasingly difficult to manage unsanctioned devices on company networks. However, once you control access to the network to authorized devices and have clear policies regarding bringing personal IoT devices, it’s easier to control the damage that Shadow IoT brings to your organization.
Related:
- Is Anyone Watching Through Your Device Cameras?
- How to Find All Devices Connected to Your Router
- 5 Ways to Prevent Your IoT Devices from Becoming a Botnet
Get the best of IoT Tech Trends delivered right to your inbox!