In a smart home system, anyone having access to your Raspberry Pi can have full control over your whole house if you’re not careful. Luckily, it’s easy to secure your Raspberry Pi and make it hacker-proof.
Here are a few things you can do to secure your Raspberry Pi and keep all the bad guys away from your smart home.
1. Set Your Username and Password Right
If you have a Raspberry Pi and haven’t touched it for a long time, chances are your username is still “pi” and password is “raspberry”.
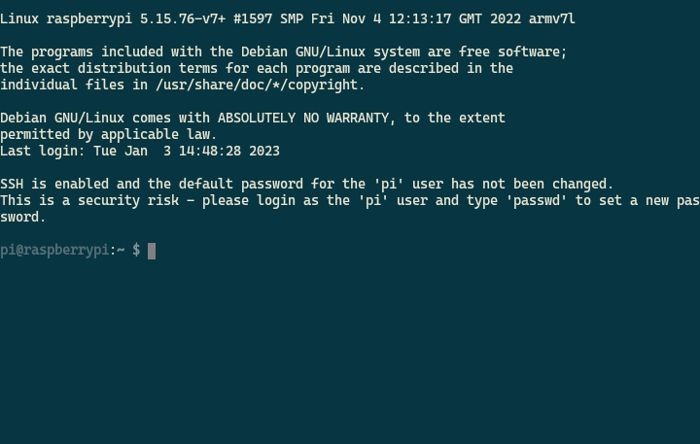
That’s the default password, or at least before the Raspberry Pi OS update in April 2022 when they removed it for safety purposes. When doing a new install, you’ll be forced to type a new username and password before it goes forward. You can’t skip it.
Of course, you can still pick “pi” and “raspberry” as your username and password. But then, you’ll get a message every time saying that you should update them soon, because having them sort of beats the reason why you even have to log in at all.
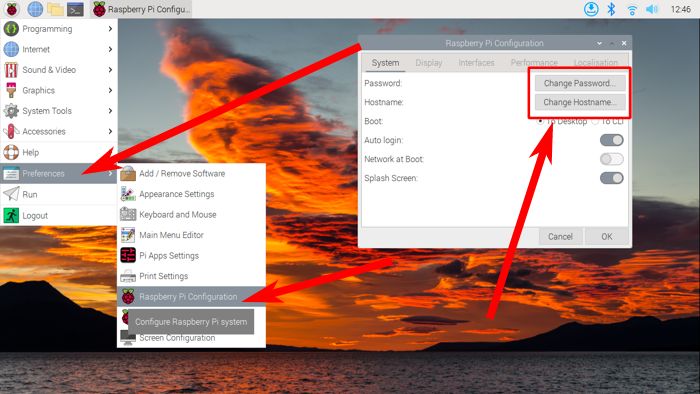
You can change your username and password by going to pi logo –> Preferences –> Raspberry Pi Configuration, then picking “Change Password…” and “Change Hostname…” to pick one that’s more secure.
2. Add a Password for sudo
When you’re using a Raspberry Pi, you’re technically using a Linux machine. And in most Linux distros, sudo (Super User DO) comes pre-installed by default. You’ll even see it used in all the different tutorials over the world wide web.
However, by default, sudo will only ask you the password once. If you want to slow down an attacker who figured out your oh-so-secure and not-really-“raspb3rry” password, then you’ll need to make it ask for the password all the time.
To do this, you’ll have to edit the sudo settings:
- Log into your Raspberry Pi and enter
sudo nano /etc/sudoers.d/010_pi-nopasswd
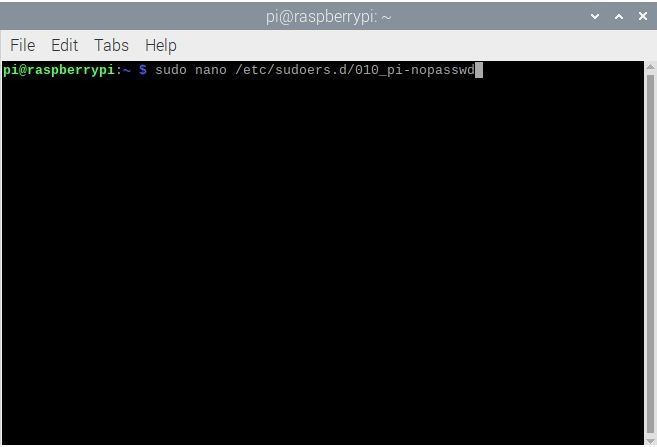
- That will open a file that has a single line:
pi ALL=(ALL) NOPASSWD: ALL. In it, replaceNOPASSWDwithPASSWD.
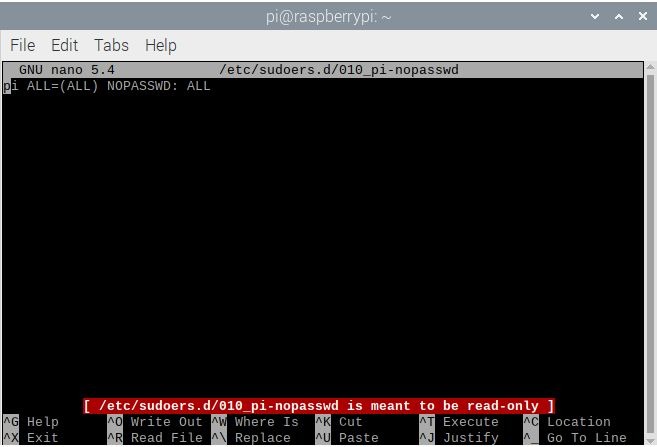
- To save your changes, press Ctrl + X on your keyboard. If it asks to save the buffer, press Y.
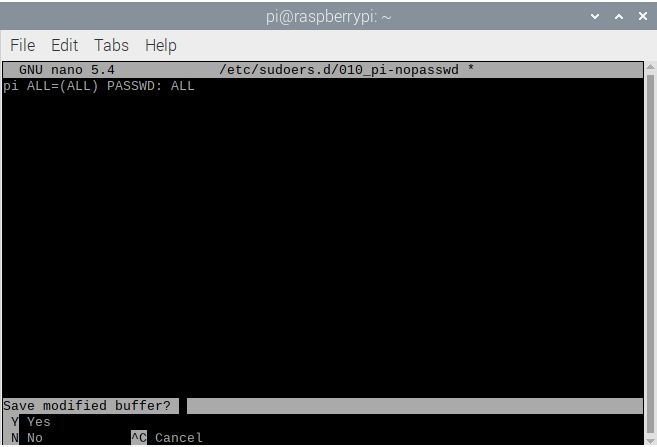
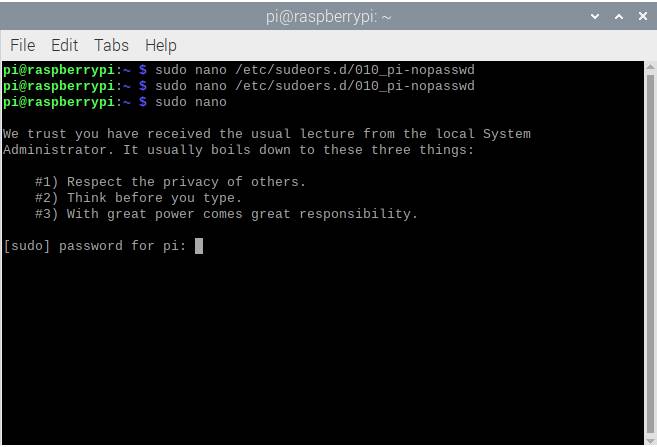
- From now on, when you use sudo, you’ll be asked to type the password.
3. Keep Your Programs Updated
Just like any other Linux distro, you’re in charge of keeping the operating system updated.

It’s not that hard, just two steps:
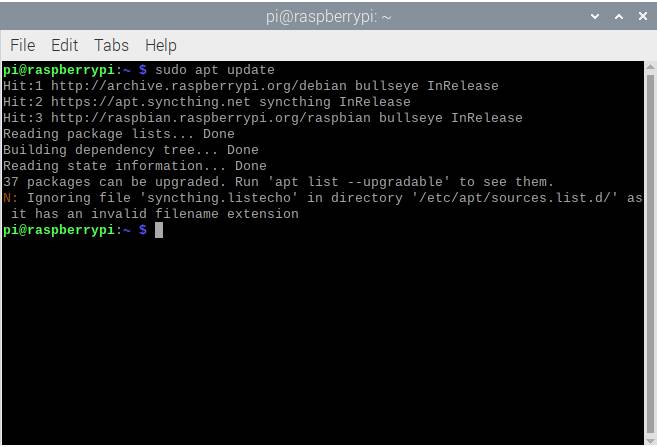
- Enter
sudo apt updatein the terminal to make apt look for all the latest versions of the programs you have installed.
- Enter
sudo apt upgradeto install the latest versions it found en masse.
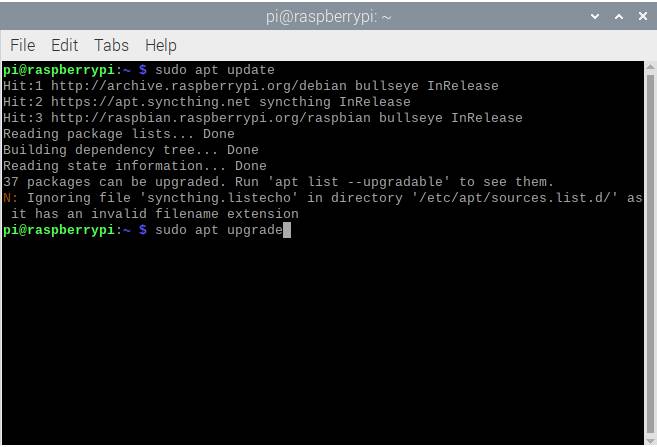
The only problem here is that after doing the second step, it’s going to take quite a while until it finishes installing everything (around 30 minutes on average). The good news is that this helps you cover for vulnerabilities in the programs you use, which should prevent malicious users from hacking into your Raspberry Pi using outdated methods.
4. Update Your Raspberry Pi OS
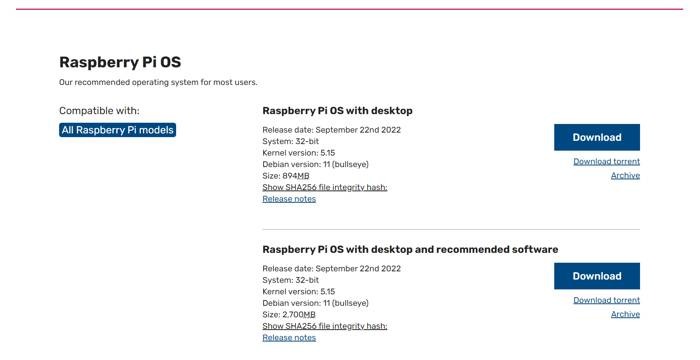
If you are using a Raspberry Pi, then you probably already know how to install the Raspberry Pi OS. But some OS updates can get so drastic, you’ll need to do a fresh install.

You can figure out if you’re using the latest OS version by going to the Raspberry Pi OS download page and checking the list. So far, the latest version is called Bullseye and is based on Debian version 11.
5. Change the Default SSH Port
Folks who use headless Raspberry Pis use SSH to control it over a phone or computer. That’s not a big problem – it saves a lot on the electricity bill after all. Just that bots can detect your active SSH device if they happen to run on a public network.
Bots typically look for devices connected under port 22 for because it’s the default port for SSH devices. You can change the SSH port number to make it more secure.
- Log into your SSH terminal and enter
sudo nano /etc/ssh/sshd_config.
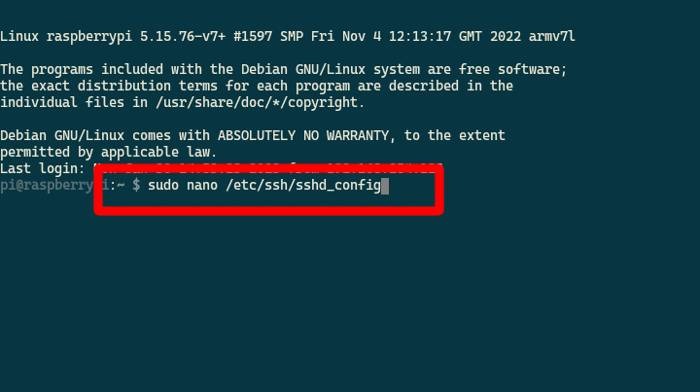
- Go through the file looking for a line that says
Port 22. Change that to a number between 1024 and 65536.
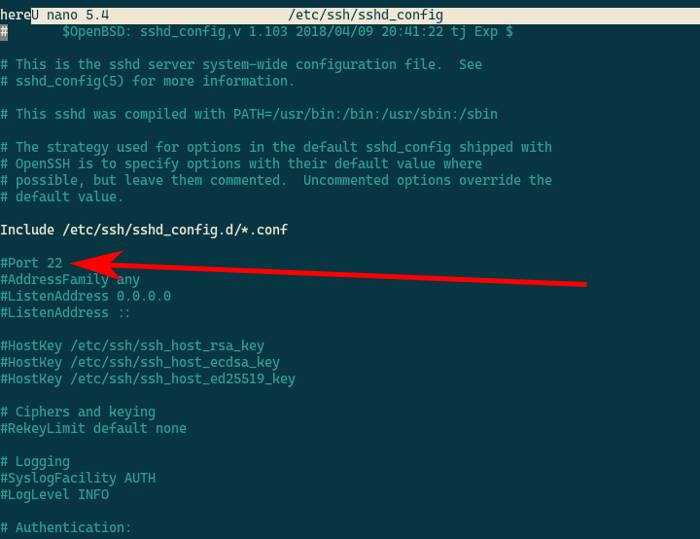
Note: All port numbers at 1024 and below are used in privileged services. This means that you’ll need to have sudo to do anything. Picking a port number from 1025 and up lets you do things without sudo, but also stops and asks for a password if you need it. This way, you can use the Raspberry Pi without risking bots sniffing out your sudo password.
Frequently Asked Questions
Is a Raspberry Pi difficult to hack?
Compared to a Windows PC with a lot of features that are open to vulnerabilities, it’s a little bit harder to even install a virus by accident on a Raspberry Pi. It doesn’t have much space for larger programs – assuming that it would even work on a Debian-based system at all. This doesn’t mean that you can forget about cybersecurity with your Raspberry Pi though. Because unlike a normal PC, you are more likely to leave this on for 24/7 with wireless functions running in the background.
What port numbers above 1024 should I not use as an alternative SSH port?
You can use any port number above 1024, but you may find a few problems if you use a port that’s also a dedicated alternative port for a different service you are using. This includes 8080 (TCP/IP), 8888 (web development), and 27017 (default MongoDB port). Alternatively, 22000 is an alternative port for SSH services. Just don’t pick a number that’s too high, since some ISPs and WiFi routers have limits on these.
Can my Raspberry Pi be hacked remotely?
If your Raspberry Pi is connected to a wireless network, there is always a risk of it being hacked remotely. This can get even worse if you have it connected to the internet, letting it get exposed to all the kinds of bots that scan for vulnerable devices. But that shouldn’t happen if you do the standard internet safety practices.
Can my Raspberry Pi be hacked through a GPIO peripheral?
This could happen, in theory, but the chances of it happening is quite low. Most projects using the Raspberry Pi’s GPIO (General Purpose Input Output) pins use a program that you, yourself, will have to make to drive the pins. These programs are usually too simple to even let you access your data in the memory card, let alone a hacker who would want to do the same. But this still potentially allows another person to use your peripherals, like hijacking your remote signals on an RF receiver to take control of a Pi-based robot.
Image source: Unsplash. Screenshots by Terenz Jomar Dela Cruz.
Get the best of IoT Tech Trends delivered right to your inbox!