As of 2018, the adoption rate of IoT devices in the consumer space is slower than what was originally thought. Sure, every smartphone is an IoT device, virtual assistant speakers are quite popular and many crave a connected appliance. Furthermore, if you have a television set, it’d better be smart, or you might be looking to convert it into a smart TV.
Beyond the media hype, though, not everyone is eager to jump on the IoT bandwagon. There are pressing security challenges due to cyber attacks which act as a brake on IoT device adoption.
How Bad Is the Situation, Exactly?
According to a latest Kaspersky Labs report, the total number of IoT malware variants detected in the first half of 2018 crossed 120,000. That is a three-fold increase over the entire previous year. These cyber attacks include botnets, DDoS attempts, crypto-jacking and brute-force intrusions to access device passwords. The latter attacks, according to the report, were used 93% of the time. One reason for it could be because many consumer devices are currently shipped with passwords that are easy to figure out.
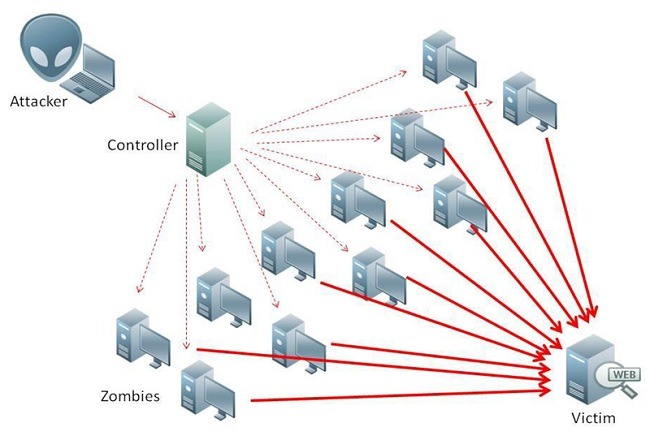
Apart from the ordinary, a number of high profile security incidents may have also led to consumer distrust. The 2016 Dyn attack, which shut down the Internet for millions of users, began as a DDoS invasion on IP cameras, access gateways and other connected devices. The Mirai botnet also struck at the same weak points, briefly taking down sites including Twitter and Spotify.
How Vulnerable Are Currently Available Devices?
Despite serious incidents above, a large part of the IoT device market remains unregulated with no uniform standards of security. The current “wait and see approach” of device manufacturers is not helping matters either. From news reports of data leaks to the possibility of a device “going rogue,” the threats are rather omnipresent. Here are a few unconfirmed incidents of popular IoT products that made news.
- Google Products: A Tripwire researcher, Craig Young, claims that using an HTML5 API, he was able to detect the GPS locations of Google Home and Chromecast users.
- Amazon Alexa: Perhaps due to reports of data leaks, less than 2% owners of Alexa devices are agreeing to make a voice purchase. A security company called Checkmarx claims that they were able to hack Alexa using a malicious code. Later they could listen to and record user conversations.
- Philips Hue: On May 31, 2018, some Hue users reported that the API synced with Alexa app went offline for four hours. This meant the device-pairing was lost. As a result, the users could not control their Hue smart lights remotely.
- Apple HomeKit: On Dec 7, 2017, 9to5mac.com reported that a security bug in Apple HomeKit for iOS 11.2 may have caused hackers to gain unauthorized access to smart devices. These would include smart locks and garage door openers. However, to Apple’s credit, they did claim to have fixed the bug immediately the next day.

It must be added, though, that while these reported incidents are far from ordinary, there is still not sufficient evidence of a large-scale disaster waiting to happen.
How Do I Secure My Device?
The truth is that just like the concerned product companies, smart device users have no choice but to “wait and watch.” However, a few precautions can indeed help you reduce your device’s exposure to potential IoT vulnerabilities.
- Have a Separate Network for Smart Devices: You might want to keep your network for smart devices separate from the one you use to browse the Internet.
- Delete your Recordings Whenever Possible: For Alexa and other voice assistants, you might want to delete your recordings, voice histories and other personal data from time to time.
- Change Device Password Defaults: While it’s becoming the norm now, the burden is on you as the consumer to use complex passwords for your devices.
- Use Two-Factor Authentication: If you’re using Google Home products, apply two-factor authentication. When your personal data passes through encrypted SSL traffic, you will feel just as secure as using Gmail.

Summary Thoughts
The rapid adoption of IoT consumer devices is not without security concerns. According to a report by Armis, nearly half a billion devices may be vulnerable to what are known as “DNS rebinding attacks” including switches, routers and access points; streaming media players and speakers; IP phones; IP cameras; printers; and smart TVs.
Here we saw how different kinds of malware utilize smartphones, tablets, and routers to gain access to your digital assistants and home IoT devices. Only time will tell if there is going to be standardization in IoT security worldwide. There was some progress very recently. Mozilla and ThingsCon just launched Trustable Technology Mark. This will help consumers know how well their IoT devices measure in terms of security.
Get the best of IoT Tech Trends delivered right to your inbox!