
The excitement around 5G is palpable even as our imagination tries to get a grip on the upcoming 5G universe. At the moment there’s a broad consensus that smartphones will become the least interesting item on the 5G menu because its true potential is far greater than earlier thought. From talking lampposts to predictive healthcare, the impact of 5G is going to be far-reaching and omnipresent.
However, there are concerns surrounding the security threats and risks of 5G. Some security researchers believe that the very attributes of 5G that make it a great improvement over 4G poses hidden security challenges. According to a Brookings study, while 5G means high speed, low latency connectivity also brings additional avenues of attacks from hackers.
Let us examine the current threat landscape of 5G and whether there is adequate cyber-preparedness due to the advent of new attack vectors.
What does the Telecom Industry Say?
On the surface, 5G is more secure than the previous spectrums. According to 3GPP, the security enhancements are being brought about in phases. The following architecture explains Phase I of 5G’s security apparatus.
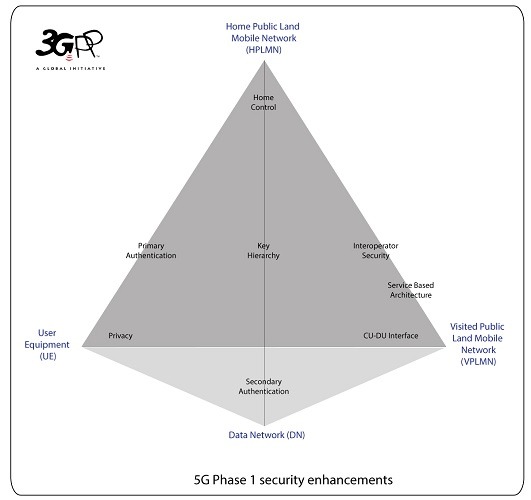
- Primary authentication: similar to 4G with minor changes due to additional key agreements.
- Secondary authentication: in contrast to 4G, there is a major change with the use of an Extensible Authentication Protocol (EAP). Apart from one-time passwords, such a protocol also supports tokens, smart cards, voice authentication, and biometrics for enhanced secure access.
- Privacy: some kind of encryption will ensure that a user’s primary user credentials are protected from unauthorized intrusions.
- Central Unit – Distributed Unit split: 5G architecture allows for splitting between user authentication credentials on a central device and distant devices on the edge. What this means is that if someone has access to your smart device, they can’t authenticate themselves locally because the authentication is being managed by a central operator server. As the authentication is tied to EAP, you needn’t worry about rogues stealing your electronic health records.
Ericsson further adds that with 5G, it won’t be possible for a hacker to identify a subscriber through IMSI catching attacks. With 2G, 3G, and even 4G, it was possible to identify a user’s credentials by tapping into the GSM base station. However, 5G will prevent long-term identity of a user to be transmitted unencrypted over radio waves.
Clearly, at the network level, a lot of thought has been at work to make 5G security foolproof. But does the technical assurance of operators match the threat scenarios on the ground?
Threat Vectors for 5G
It is very reassuring to talk about 5G running on encrypted networks controlled by EAP while separating the central node and edge networks. However, are the security teams managing IoT networks prepared for just one, single data breach?
The biggest threat vector for 5G is due to the pervasiveness of its application. It is to be used in sensitive areas such as healthcare, transportation,, big data, machine learning, artificial intelligence, and with identity-based access controls.
For a determined hacker, nothing spells greater joy than stealing someone’s personal and financial information online. Still, the damages are recoverable. While no one wants their phone stolen, at least most of us can live without it. But with 5G, it may have all changed.
Electronic Warfare is Magnified in 5G Era
In the 5G era the threats are magnified many times over because of the stakes involved. The hacker not only has a computer and phone at their disposal but far more important things that people’s lives depend on. Think of electricity grids, financial systems, transportation networks, healthcare apps, and even smart toilets. The motivation to hurt people and countries just got bigger.
Many military researchers are discussing the threats due to the weaponization of the electromagnetic spectrum. Bad actors and governments can use electromagnetic pulse (EMP) weapons to bring a country’s entire digital infrastructure and telecom networks to a grinding halt.

Here’s how it can happen: Basically, all forms of telecom and Internet communications occur over an electromagnetic spectrum consisting of seven different wavelengths. If you have non-nuclear EMP weapons carried over 5G, the intense pulse can simply melt down a vital infrastructure such as an electricity grid. At the moment, many countries – including the U.S., Israel, China, Russia, and North Korea – are reported to be working on EMP weapons. It will create a new level of threat for a nation’s infrastructure lifeline.
You may have noticed how Huawei products were banned in the United States and some other countries. The 5G equipment servicing the network may be the biggest threat at the point of installation.
Conclusion
5G is expected to become a significant disruptor in our way of life just like many other groundbreaking technologies. There is also research going on right now in 6G which will have speeds up to 1 Terabyte/second (~1024 Gbps). Clearly, we are moving to an era of ultra-high speed networks. However, the security stakes can no longer be ignored because of the level of the unintended consequences 5G might bring.









