
Cities are becoming connected through smart city initiatives focused on transport, traffic patterns, weather, and the functionality of public utilities such as lighting, parking meters, smart traffic lights, buildings, transport, and waste collection. These initiatives involve the deployment of high-bandwidth and latency-sensitive apps that draw information from multiple sources.
These enable cities to save money, reduce inefficiencies, gain valuable data to assist with town planning, resource distribution, and create citizen-centric services. However, deployed incorrectly, without the appropriate security safeguards, they also expose the risk of cyberattack by state agents or other nefarious actors who could not only access confidential data but gain control of or override the function of critical infrastructure.
Cyberattacks could generate significant damage on a city and its residents, including the shutdown or compromise of vital services, such as electricity or water. In numerous cases, ransomware attacks have even locked city staff off from municipal computers and networks, bringing operations to a halt until large payments are made.
Cyberattacks could also lead to the capture and misuse of citizens’ sensitive personal information or video footage of their activities. In January 2021, a cyberattack even allowed an outsider to temporarily alter chemical concentrations in a local water supply system.
This week, a report was published by researchers to help local-level policymakers better understand how cyber-risks vary among different smart city technologies. The research project was authored by Karen Trapenberg Frick, associate professor in the Department of City and Regional Planning at UC Berkeley, and Alison E. Post, associate professor of Political Science and Global Metropolitan Studies at UC Berkeley, along with several doctoral candidates.
The report follows a 2020 survey in which 76 cybersecurity experts ranked different technologies according to underlying technical vulnerabilities, their attractiveness to potential attackers, and the potential impact of a successful serious cyberattack.
Survey findings show the vulnerability of cities against cyberattack
Cybersecurity experts indicated that some smart city technologies present greater risks than others. These differences can be attributed to the fact that those technologies perceived as more vulnerable in technical terms are also most likely to generate the largest impacts in the event of a successful attack and to attract the attention of effective threat actors. Attackers like the brag factor of causing havoc in a way that is likely to be reported by the media.
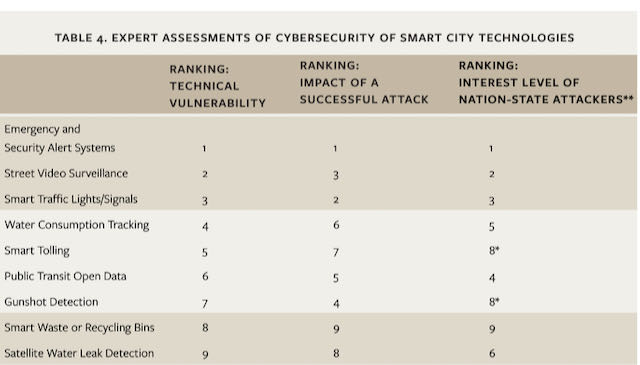
Significantly, the technologies perceived by respondents as most vulnerable to a cyberattack are also ranked as those that are most likely to generate significant impacts in the event of a successful attack. Emergency and security alert systems, street video surveillance, and smart traffic lights were ranked as significantly more vulnerable to cyberattacks; moreover, respondents viewed cyberattacks on these technologies as likely to generate a significantly higher impact if successful.
In contrast, smart waste or recycling bins and satellite water leak detection were ranked as significantly less vulnerable and lower impact compared to other technologies.
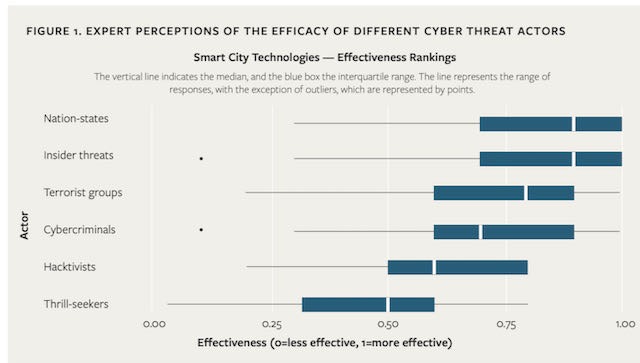
Surveyed experts indicated that nation-states and insiders would be most effective at executing cyberattacks, compared with thrill-seekers, cybercriminals, terrorist groups, and hacktivists. Responses to our open-ended questions indicate that the experts consider nation-states to possess strong motives for attacks on infrastructure and to be able to mobilize the significant resources needed to launch attacks from the outside.
Insiders, meanwhile, have easy access and the skills and knowledge to carry out effective attacks. Crucially, the surveyed experts indicated that the three technologies ranked as most vulnerable and impactful would be of the greatest interest to nation-states: emergency or security alerts, street video surveillance, and smart traffic lights or signals.
In 2018, Hawaii’s Emergency Management Agency mistakenly sent out an emergency message: “BALLISTIC MISSILE THREAT INBOUND TO HAWAII. SEEK IMMEDIATE SHELTER. THIS IS NOT A DRILL.”
This was sent to Hawaii residents and vacationers. It also went out to televisions and radios. This was, fortunately, a false alarm, but it took the agency 38 minutes to send a second alert confirming the message was a false alarm.
The intersection of public and private infrastructure is a cyberhacking sweet spot
Most people will recall the WannaCry ransomware attack with over 50,000 organizations and 150 countries hit. In the U.K., an attack against the National Health Service (NHS) left staff unable to access patient records, some phones went down and surgeons cancelled operations. In Germany, digital display boards at Deutsche Bahn train stations were inoperable. The attack in Spain left internal computers down at telecommunications provider Telefonica.
Public transport is an attractive attack space for cybercriminals. A ransomware attack occurred in 2016 on San Francisco’s transit system. Station agent booth monitors read: “You Hacked. ALL data encrypted,” and the culprit allegedly demanded 100 Bitcoin (about $73,000).
In a statement, the SFMTA said it turned off payment machines and opened the gates as a precaution, meaning that the attack was, fortunately, brief and contained. It’s not the first attack on public transport.
In 2008, in the Polish city of Lodz, four trams derailed, and the attack forced others to make emergency stops. The attack injured twelve people. Police later found that a teenager hacked the tram system by using open-source information and trespassing into tram depots, taking control of a vehicle and the points system (one of the few physical trespass examples in a city cyberattack).
In 2014, the hackers targeted the Chinese national train reservation system, stealing customers’ personal data. All of this suggests that public transport is an appealing target to those wanting to cause array with the right know-how.
But cyberattackers don’t even need IoT to attack a city
It’s easy to point the finger at IoT as the symptom of all that is evil when it comes to cyberattacks against cities. Cyber attacks on local municipalities are increasing – and they don’t even need IoT to get access. Cities – smart or otherwise – have been a buffet for state agents looking to make a quick buck. Many city officials opt to pay a ransom to regain access to their systems and data. In 2019, there were at least 104 ransomware attacks against administrative systems in schools and governments, according to cybersecurity company Recorded Future.
It’s a problem compounded by cities with tight IT and security budgets. This results in the use of out-of-date software and poor adherence to running security updates. Staff may be inadequately trained in cybersecurity awareness of practices, such as email phishing.
All in all, it means that if a hacker wants to break into city databases, there are likely to be rewards. For example, the act of switching off CCTV cameras could obscure other crimes taking place. Attacks could also be not only inconvenient but potentially life-threatening if attackers took control of traffic lights, toll gates, or emergency alerts.
Protecting cities needs a multi-agency approach
Last week, the U.S. Secret Service hosted a virtual Cyber Incident Response Simulation. State and municipal government officials focused on ransomware attacks and mitigation strategies. Executives in cyber incident response roles used a simulated scenario to enhance planning, collaboration, and information sharing between state and local government agencies and the Secret Service. The role-play simulation allowed participants to better understand how to efficiently and effectively respond to a ransomware attack. The event featured guest speakers from the Federal Bureau of Investigation, National Guard Bureau, Cybersecurity and Infrastructure Security Agency, and other law enforcement leaders.
Get the best of IoT Tech Trends delivered right to your inbox!










